How Asymetric Public Private Key Pairs Are Generated
Posted : admin On 25.05.2020- How Asymmetric Public Private Key Pairs Are Generated Mean
- How Asymmetric Public Private Key Pairs Are Generated 2017
- How Asymmetric Public Private Key Pairs Are Generated In Spanish
Asymmetric, or public/private encryption, uses a pair of keys. Data encrypted with one key are decrypted only with the other key in the public/private key pair. When an asymmetric key pair is generated, the public key is typically used to encrypt, and the private key is typically used to decrypt. Oct 12, 2016 Angela from the API support team walks through how to generate a public private key pair using OpenSSL and register a private application. If you want to try integrating to Xero, partner. How can one securely generate an asymmetric key pair from a short passphrase? How can a user can get a public and private key without the server saving/knowing the private key. The password needs to be sufficiently long and sufficiently random that the associated key space of asymmetric keys generated from password data is large.
Cryptography
A key is the basis for a transformation, usually mathematical, of an ordinary message into an unreadable message. For centuries, most encryption systems have relied on private key encryption. Public key encryption is the only challenge to private key encryption that has appeared in the last 30 years. The public key is usually easy to derive from the private key. For RSA the public exponent may not be known, but it is usually set to a fixed number (65537). This together with the modulus - also part of the private key - makes the public key. When an ICA client session is initiated, a unique public/private key pair is generated and passed through the communications channel. Once communication is established, these key pairs are used to arrive at the same RC5 symmetric key. Using a 1024-bit symmetric key, the client then begins processing ICA traffic and log-on information. A random public/private key pair is generated when a new instance of the class is created. RSACryptoServiceProvider RSA = new RSACryptoServiceProvider; Once keys are generated, we can use ToXmlString or ExportParameters method to read the keys.
Note that it is useful only when we need to delete rows from comparison table.The option in table comparison do not generate keys for the target table. Key generation function in bods. Hi Praveen,They are completely different.Generated Key option in table comparison tells Data Services how to handle the case 'more than one deleted rows with the same key value': compare all rows or compare the rows with the largest generated key value.
Derrick Rountree, in Security for Microsoft Windows System Administrators, 2011
Asymmetric Encryption
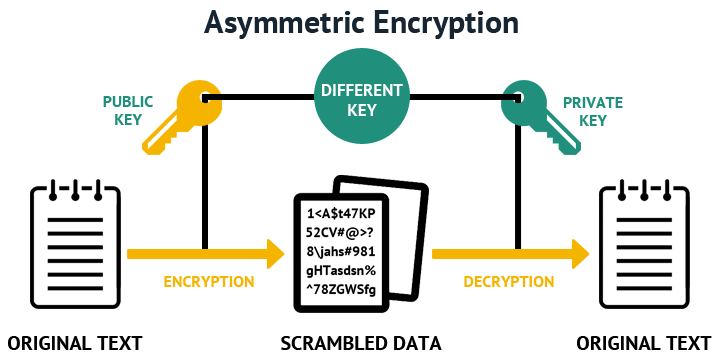
Asymmetric encryption is also referred to as public key encryption. In asymmetric encryption, both the encrypting and decrypting systems have a set of keys. One is called the public key, and another is called the private key. If the message is encrypted with one key in the pair, the message can be decrypted only with the other key in the pair.
Asymmetric key algorithms are not quite as fast as symmetric key algorithms. This is partially due to the fact that asymmetric key algorithms are generally more complex, using a more sophisticated set of functions.
Asymmetric Key Algorithms
Asymmetric key algorithms aren't as widely used as their symmetric counterparts. So we'll just go over two of the big ones: Diffie-Hellman and RSA.
Diffie-Hellman: The Diffie-Hellman algorithm was one of the earliest known asymmetric key implementations. The Diffie-Hellman algorithm is mostly used for key exchange. Although symmetric key algorithms are fast and secure, key exchange is always a problem. You have to figure out a way to get the private key to all systems. The Diffie-Hellman algorithm helps with this. The Diffie-Hellman algorithm will be used to establish a secure communication channel. This channel is used by the systems to exchange a private key. This private key is then used to do symmetric encryption between the two systems.
RSA: It is the Rivest Shamir Adelman algorithm. RSA was developed in 1978. RSA was the first widely used asymmetric algorithms used for signing and encryption. It supports key lengths of 768 and 1,024 bits. The RSA algorithm uses a three-part process. The first part is key generation. The keys used in the RSA algorithm are generated using mathematical operations based on prime numbers. The second part of the process is encryption. This encryption is done using one of the keys in the key pair. The third part of the process is decryption. The decryption is done using the other key in the key pair.
Read full chapterAsymmetric keys, also known as public/private key pairs, are used for asymmetric encryption. Asymmetric encryption is used mainly to encrypt and decrypt session keys and digital signatures. Asymmetric encryption uses public key encryption algorithms.
Public key algorithms use two different keys: a public key and a private key. The private key member of the pair must be kept private and secure. The public key, however, can be distributed to anyone who requests it. The public key of a key pair is often distributed by means of a digital certificate. When one key of a key pair is used to encrypt a message, the other key from that pair is required to decrypt the message. Thus if user A's public key is used to encrypt data, only user A (or someone who has access to user A's private key) can decrypt the data. If user A's private key is used to encrypt a piece of data, only user A's public key will decrypt the data, thus indicating that user A (or someone with access to user A's private key) did the encryption.
If the private key is used to sign a message, the public key from that pair must be used to validate the signature. For example, if Alice wants to send someone a digitally signed message, she would sign the message with her private key, and the other person could verify her signature by using her public key. Because presumably only Alice has access to her private key, the fact that the signature can be verified with Alice's public key indicates that Alice created the signature.
Unfortunately, public key algorithms are very slow, roughly 1,000 times slower than symmetric algorithms. It is impractical to use them to encrypt large amounts of data. In practice, public key algorithms are used to encrypt session keys. Symmetric algorithms are used for encryption/decryption of most data.
Similarly, because signing a message, in effect, encrypts the message, it is not practical to use public key signature algorithms to sign large messages. Instead, a fixed-length hash is made of the message and the hash value is signed. For more information, see Hashes and Digital Signatures.
How Asymmetric Public Private Key Pairs Are Generated Mean
Each user generally has two public/private key pairs. One key pair is used to encrypt session keys and the other to create digital signatures. These are known as the key exchange key pair and the signature key pair, respectively.
How Asymmetric Public Private Key Pairs Are Generated 2017
Note that although key containers created by most cryptographic service providers (CSPs) contain two key pairs, this is not required. Some CSPs do not store any key pairs while other CSPs store more than two pairs.
How Asymmetric Public Private Key Pairs Are Generated In Spanish
All keys in CryptoAPI are stored within CSPs. CSPs are also responsible for creating the keys, destroying them, and using them to perform a variety of cryptographic operations. Exporting keys out of the CSP so that they can be sent to other users is discussed in Cryptographic Key Storage and Exchange.