Public Private Key Generation In Unix
Posted : admin On 26.05.2020- Public Private Key Generation In Unix Software
- Public Private Key Generation In Unix 2017
- Free Key Generation Software
- Public Private Key Generation In Unix Server
Aug 17, 2017 use this online tool igolder to generate key pair keep the private key with you and share the public key with third party, but do remember the password which you provide in that website while generating that key pair you need that one in module configuration check this blog for more details on PGP decryption. May 17, 2019 We can generate ssh key pair on Unix using ssh-keygen utility. This comes under openssh in all Unix flavour Run the ssh-keygen ssh-keygen -b 2048 -t rsa rsa: it is the algorithm for generating the public -private key pair 2048: it is bit size ssh-keygen -b 2048 -t rsa Generating public/private rsa key pair. The simplest way to generate a key pair is to run ssh-keygen without arguments. In this case, it will prompt for the file in which to store keys. Here's an example: klar (11:39) ssh-keygen Generating public/private rsa key pair.
Aug 07, 2019 How do I set up public key authentication? You must generate both a public and a private key pair. For example: Fig.01: Our sample setup Where, server1.cyberciti.biz – You store your public key on the remote hosts and you have an accounts on this Linux/Unix based server. Hi, we have private and public key, encrypt file using public and want to decrypt using private key. Can you please advise below commands are correct or other remedy if unix have? Encrypt -a arcfour -k publickey.asc -i TESTFILE.csv -o TESTFILE00.csv decrypt -a arcfour -k privatekey.asc.
How to Generate a Public/Private KeyPair for Use With Solaris Secure Shell
Users must generate a public/private key pair when their site implementshost-based authentication or user public-key authentication. For additionaloptions, see the ssh-keygen(1) manpage.
Before You Begin
Public Private Key Generation In Unix Software
Determine from your system administrator if host-based authenticationis configured.
Start the key generation program.
where -t is the type of algorithm, one of rsa, dsa, or rsa1.
Specify the path to the file that will hold the key.
Bydefault, the file name id_rsa, which represents an RSAv2 key, appears in parentheses. You can select this file by pressing the Return key. Or, you can type an alternative file name.
The file name of the public key is created automatically by appendingthe string .pub to the name of the private key file.
Type a passphrase for using your key.
This passphraseis used for encrypting your private key. A null entry is stronglydiscouraged. Note that the passphrase is not displayed when youtype it in.
Retype the passphrase to confirm it.
Check the results.
Gitkraken will use your computers own ssh agent which we have configured to authenticate us successfully.Hope this helps some.Update: I also had to include ssh-add -K /.ssh/idrsa inside my /.bashprofile to make it load automatically, otherwise you'll have to run that command on every computer restart. Generate ssh key for bitbucket mac. Now when you do git fetch from terminal or do git fetch from Gitkraken, it should both work.
Check that the path to the keyfile is correct.
At this point, you have created a public/private key pair.
Choose the appropriate option:
If your administrator has configuredhost-based authentication, you might need to copy the local host's publickey to the remote host.
You can now log in to the remote host.For details, see How to Log In to a Remote Host With Solaris Secure Shell.
Type the command on one line with no backslash.
When you are prompted, supply your login password.
If your site uses user authentication with public keys, populateyour authorized_keys file on the remote host.
Copy your public key to the remote host.
Type thecommand on one line with no backslash.
When you are prompted, supply your login password.
Whenthe file is copied, the message “Key copied” is displayed.
(Optional) Reduce the prompting for passphrases.
For a procedure, see How to Reduce Password Prompts in Solaris Secure Shell. For more information, see the ssh-agent(1) and ssh-add(1) man pages.
Example 19–2 Establishing a v1 RSA Key for a User
Public Private Key Generation In Unix 2017

Free Key Generation Software
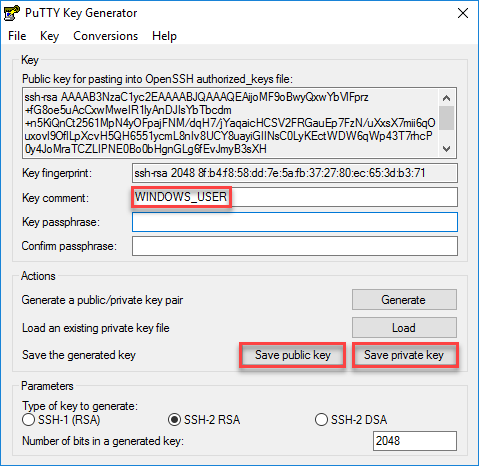
In the following example, the user cancontact hosts that run v1 of the Solaris Secure Shell protocol. To be authenticated by v1hosts, the user creates a v1 key, then copies the public key portion to theremote host.