Text Manipulation Procedures For Primary Key Generation
Posted : admin On 30.05.2020- Text Manipulation Procedures For Primary Key Generation 2
- C# Text Manipulation
- Text Manipulation Procedures For Primary Key Generation 2
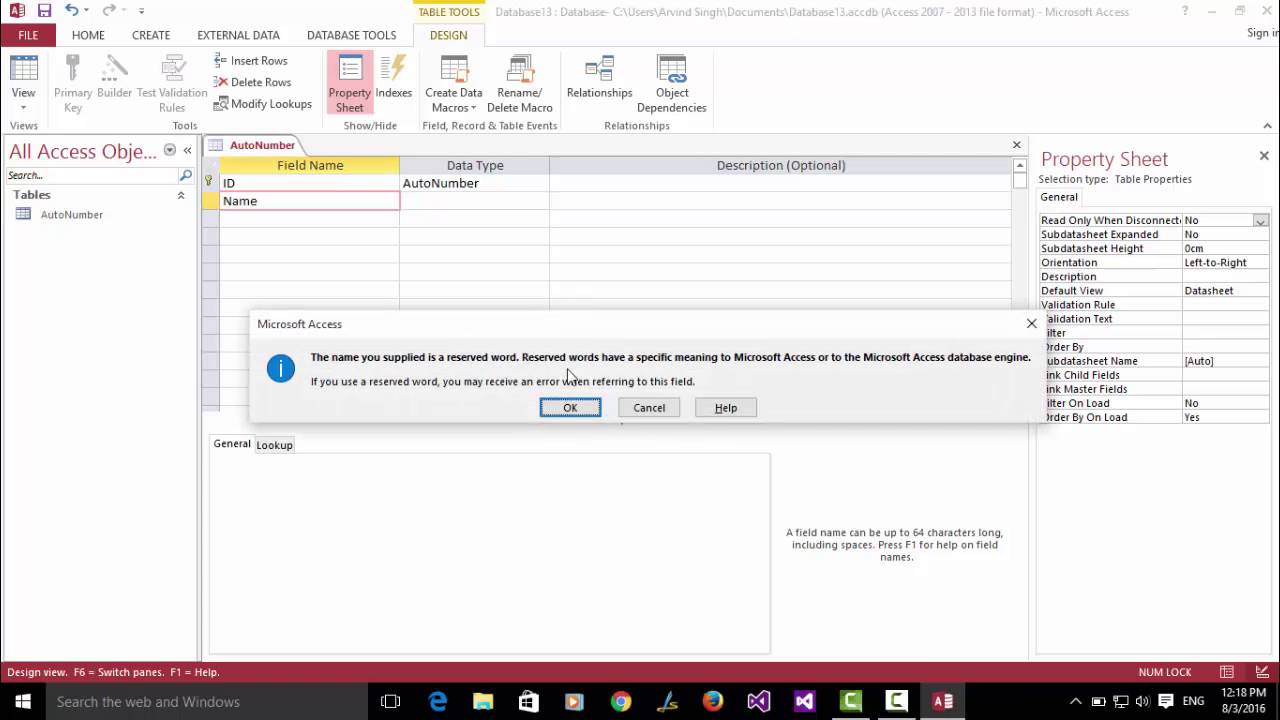
In this paper we are presenting a DNA encryption technique based on matrix manipulation and secure key generation scheme. Do you want to read the rest of this conference paper? Request full-text. Sep 19, 2013 In this post, we demonstrate a couple of different ways to set the primary key in MS Access. A Primary Key is defined as “a unique key that can uniquely identify each row in a table”. The actual Key itself can be an auto-generated ID number, a known unique number (such as a social security number) or even a text field.
The Wolfram Language has uniquely flexible capabilities for processing textual data. It can operate at the level of strings and characters or at the level of words and sentences. It can also operate semantically, through its extensive built-in natural language understanding capabilities.
Text Acquisition
Import— import text from files or the web
'Text', 'PDF', 'TeX', 'HTML'— pick out plaintext, table data, etc.
NotebookImport— import text from a notebook
FindList— search files for records containing particular strings
TextString— convert arbitrary expressions to text
TextRecognize— extract text from images using OCR
ToLowerCase ▪ ToUpperCase ▪ RemoveDiacritics ▪ CharacterEncoding ▪ ..
DeleteStopwords— delete standard stopwords ('the', 'and', etc.) from a string Iron front liberation 1944 cd key generator download no survey no password.
StringSplit— split a string at newlines or other delimiters
StringReplace ▪ StringDelete ▪ StringTrim ▪ ..
Structural Text Manipulation
TextCases— extract symbolically specified elements
TextSentences— extract a list of sentences
TextWords— extract a list of words
SequenceAlignment— find matching sequences in text
StringExpression— general string pattern
StringMatchQ ▪ StringCases ▪ StringCount ▪ ..
WordCounts— count occurrences of words and -grams
LetterCounts ▪ CharacterCounts ▪ WordCount
Classify— classify strings based on training data or built-in classifiers
Natural Language Processing
LanguageIdentify— determine the language of a text
DictionaryLookup— look up words in English and other dictionaries
WordData— find semantic, grammatical, morphological, etc. properties of words
TextStructure— parse text into its grammatical structure
TextContents— generate a dataset of identified elements in text
SpellingCorrectionList— list of spelling suggestions for misspelled words
Interpreter— attempt to interpret strings of a wide variety of types
SemanticInterpretation ▪ SemanticImportString ▪ AmbiguityFunction ▪ ..
StringTemplate ▪ StringRiffle ▪ TextString ▪ Pluralize ▪ ..
- ▪▪▪▪
- ▪▪▪▪▪
SQL PRIMARY KEY Constraint
The PRIMARY KEY constraint uniquely identifies each record in a table.
Primary keys must contain UNIQUE values, and cannot contain NULL values.
A table can have only ONE primary key; and in the table, this primary key can consist of single or multiple columns (fields).
SQL PRIMARY KEY on CREATE TABLE
The following SQL creates a PRIMARY KEY on the 'ID' column when the 'Persons' table is created:
MySQL:
ID int NOT NULL,
LastName varchar(255) NOT NULL,
FirstName varchar(255),
Age int,
PRIMARY KEY (ID)
);
SQL Server / Oracle / MS Access:
ID int NOT NULL PRIMARY KEY,
LastName varchar(255) NOT NULL,
FirstName varchar(255),
Age int
);
To allow naming of a PRIMARY KEY constraint, and for defining a PRIMARY KEY constraint on multiple columns, use the following SQL syntax:
MySQL / SQL Server / Oracle / MS Access:
ID int NOT NULL,
LastName varchar(255) NOT NULL,
FirstName varchar(255),
Age int,
CONSTRAINT PK_Person PRIMARY KEY (ID,LastName)
);
Note: In the example above there is only ONE PRIMARY KEY (PK_Person). However, the VALUE of the primary key is made up of TWO COLUMNS (ID + LastName).
SQL PRIMARY KEY on ALTER TABLE
To create a PRIMARY KEY constraint on the 'ID' column when the table is already created, use the following SQL:
MySQL / SQL Server / Oracle / MS Access:
May 16, 2019 Creating a masterkey and importing this key with the extended private key into Electrum gives other addresses than with this library. And sending coins to. I can only find algorithms to generate addresses from the master private key but according to Stack Exchange Network Stack Exchange network consists of 175 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn, share their knowledge, and build their careers. There are numerous payment systems such as Bitpay that do all the hard work for you. The drawback is that they are in charge of your private keys. You may implement your own simple solution using an extended public key (XPUB) from a hierarchically deterministic (HD) wallet, however. The whole process is explained in BIP 32. Currently I have some working php code to generate a private/public keypair and store them in two variables. These variables are strings, with one variable containing the private key, and the other containing the public key. I researched on stack overflow and I also found some code to convert a pem encoded key string to a der encoded key string. Bitwasp php generate private key. PHP bitwaspbitcoinkey PrivateKeyFactory - 17 examples found. These are the top rated real world PHP examples of bitwaspbitcoinkeyPrivateKeyFactory extracted from open source projects. You can rate examples to help us improve the quality of examples.
To allow naming of a PRIMARY KEY constraint, and for defining a PRIMARY KEY constraint on multiple columns, use the following SQL syntax:
MySQL / SQL Server / Oracle / MS Access:
ADD CONSTRAINT PK_Person PRIMARY KEY (ID,LastName);
Note: If you use the ALTER TABLE statement to add a primary key, the primary key column(s) must already have been declared to not contain NULL values (when the table was first created).

Text Manipulation Procedures For Primary Key Generation 2
DROP a PRIMARY KEY Constraint
To drop a PRIMARY KEY constraint, use the following SQL:
C# Text Manipulation
MySQL:
SQL Server / Oracle / MS Access: